ストラッシュ川口 口コミや評判
ストラッシュ川口 口コミや評判
ストラッシュ川口の口コミや評判は、以下のようなものがあります。
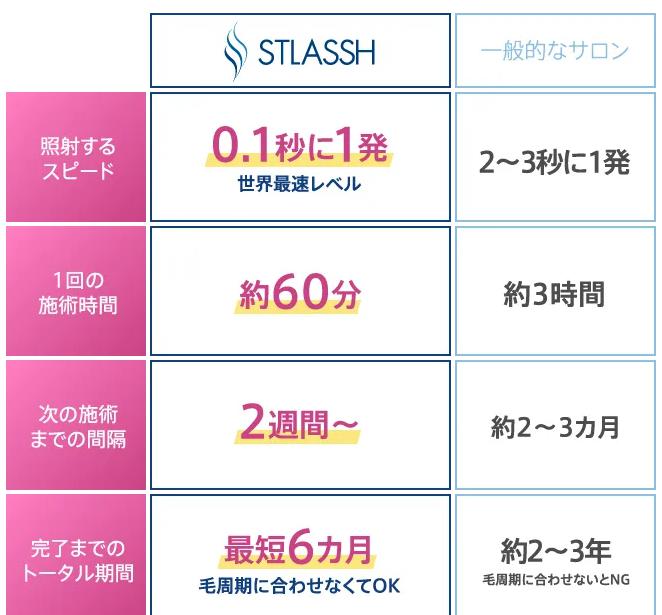
施術時間が短くて早く終わる
痛みが少なくて肌への負担が軽い
日焼け肌や自黒肌でも脱毛できる
施術回数が多くて脱毛効果が高い
料金プランが安くてコスパがいい
予約が取りやすくてキャンセル料もない
概ね好評な口コミが多いですが、一部に以下のような不満や悪い評判もあります。
効果が出にくくて何度も通わないといけない
予約が取れないことがある
店舗間の移動ができない
カウンセリング時に勧誘されることがある
以上のように、ストラッシュ川口の口コミや評判は、メリットとデメリットがあります。
自分の目的や予算に合わせて判断すると良いでしょう。
STLASSH川口店の詳細
| 店舗名 | STLASSH川口店 |
|---|---|
| 住所 | 埼玉県川口市本町4-1-4
川口イーストビル5F |
| 営業時間 | 12:00〜21:00 |
| ベッド数 | 6台 |
| 最寄り駅 | 「川口駅」徒歩3分 |
| 駐車場 | なし |
| 地図 |
ストラッシュ川口の口コミ
1年くらい通っていますが、店内はいつも清潔で、店員さんもとても丁寧に施術して頂いているので快適です!
別の店舗にも行ったことあるのですが、川口店が1番施術がスムーズなのと落ち着いてる雰囲気があるので通いやすいです。
引用元: 引用
店員さんがとても丁寧に施術してくれます。前は池袋、大宮でも施術しましたが、
そちらの店員さんとても丁寧に施術してくれました。
ストラッシュさんは、接客態度がいつも良いのでオススメです。
1人か2人で施術してくれます。
2人だと全身30分位で終わりました。引用元: 引用
初めての脱毛に不安を感じていましたが、店員さんがとても優しく丁寧に対応してくれました!痛みもほとんど感じず、肌の調子も来店した時よりもちもちになった気がします。
販売しているスキンケアもたくさんの種類があり気になりました!
引用元: 引用
いつも親切で柔らかい対応をしてくださり、こちらのミスがあった際にも嫌な顔せずご対応いただき、さすがだなあと思っています。
なんだかんだと長く通っていますが肌トラブルが起こったことは一度もないです。エレクトロポーションも施術していただきましたが、こちらは独特の感触で強めのEMSのようなグニグニした感じがあります。いずれにせよ施術後はいつも心なしか肌がもっちりします。
最近予約も取りやすくなって施術時間も短くなった(ように感じる)ので、引き続きお世話になりたいです。引用元: 引用
普段他店舗で施術を行っていて、川口店は初めての利用でした。2人での施術は何度も経験していましたが、30分ほどで終わったのでとてもスムーズで驚きました。また、室内がとても暖かく、真冬の寒い時期でもあまりストレスを感じずに過ごせました。店員さんの対応など全体的にサービスの質が高く、とてもいい店舗だと思います。
引用元: 引用
ストラッシュ川口の料金プラン

ストラッシュ川口の料金プランは、以下のようなものがあります。
新全身ライト脱毛コース
6回で総額125,400円(税込)または月々2,900円(税込)から
新全身スタンダード脱毛コース
6回で総額150,400円(税込)または月々3,500円(税込)から
顔脱毛コース
6回で総額58,870円(税込)または月々2,000円(税込)から
デリケートゾーン脱毛コース:6回で総額47,760円(税込)または月々2,000円(税込)から
全身脱毛月額制コース
月々4,400円(税込)
以上のように、ストラッシュ川口の料金プランは、一括払いと分割払いの両方が選べるようになっています。
また、学割やペア割などの割引やキャンペーンもありますので、詳しくは公式サイトをご覧ください。
ストラッシュ川口の脱毛方法
ストラッシュ川口の脱毛方法は、以下のようなものがあります。
SHR脱毛
光を照射することで毛根にダメージを与えて毛の再生を阻止する方法です。
痛みが少なく、日焼け肌や自黒肌にも対応できます。
うぶ毛にも効果があります。
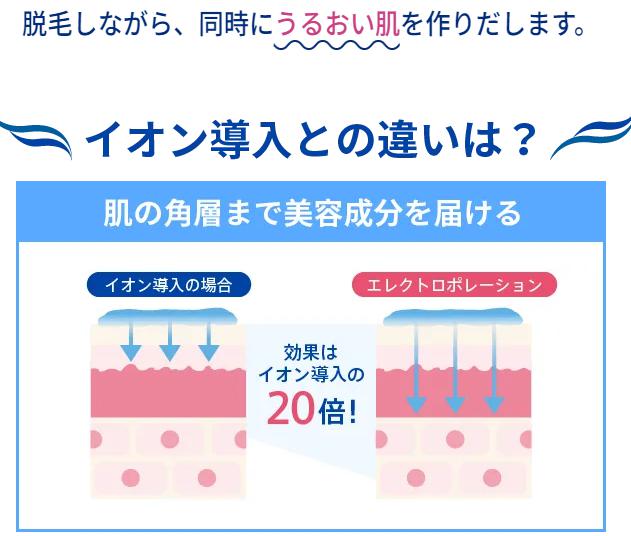
エレクトロポレーション脱毛
SHR脱毛と同時に美容成分たっぷりのジェルをお肌の奥まで届ける方法です。
イオン導入の約20倍の浸透力があり、美肌効果も期待できます。
ハダテラスフェイスマスク
エレクトロポレーション脱毛の後に使用するフェイスマスクです。
ヒアルロン酸やコラーゲンなどの保湿成分が含まれており、ワントーン明るくハリのある肌に仕上げます。
以上のように、ストラッシュ川口の脱毛方法は、脱毛と美肌を同時に目指せるものが多いです。
自分のお肌や毛質に合わせて選ぶと良いでしょう。
ストラッシュ川口の予約方法
ストラッシュ川口の予約方法は、以下のようなものがあります1234。
公式サイト:ストラッシュのホームページから「ご予約・お問合わせ」フォームに必要事項を入力して送信すると、予約が完了します。
予約状況やキャンセル待ちも確認できます。
電話:営業時間内に電話をかけて、希望の日時やコースを伝えると、予約が完了します。
キャンセルや変更も電話で行えます。
LINE:ストラッシュの公式LINEアカウントを友だち追加すると、LINEからも予約ができます。
メニューから「ご予約」を選択して、希望の店舗や日時を入力すると、予約が完了します。LINEではお得なキャンペーン情報や脱毛に関する豆知識なども配信されます。
以上のように、ストラッシュ川口の予約方法は、公式サイト、電話、LINEの3つから選べます。
自分に合った方法で予約してみてください。
ストラッシュ 川口店豊富なメニュー
脱毛サロンで脱毛を検討する際には、数あるサロンの中から自分に合った店舗を選ぶことが大切です。
中でも、痛みの少なさや効果が期待できる脱毛方法を導入しているストラッシュ 川口店は、おすすめのサロンの1つです。
全身61部位もできる人気の全身脱毛や、美肌効果が期待できるエレクトロポレーション脱毛など、豊富なメニューを用意しています。
また、初めての方でも安心して施術を受けられる無料カウンセリングも行っているため、ぜひ足を運んでみてください。
痛みが少なく、産毛や日焼け肌にも効果が期待できるSHR脱毛を導入
ストラッシュ 川口店では、女性限定の脱毛サロンで痛みが少なく、産毛や日焼け肌にも効果が期待できるSHR脱毛を導入しています。
このSHR脱毛は、肌表面の色素に反応するのではなく、肌内部の毛包に働きかけるため、従来の脱毛方法と比較すると肌に温かみを感じる程度で脱毛ができます。
また、高温で光を照射するのではなく、低温での連続照射のため、肌トラブルも防ぐことができます。
産毛や日焼け肌にも効果が期待できるため、お肌にお悩みがある方にもぴったりです。
全身61部位もOK!たった60分で施術可能
ストラッシュ川口店では、女性限定の脱毛サロンとして、痛みが少なく、産毛や日焼け肌にも効果が期待できるSHR脱毛を導入しています。
1度のご来店で全身61部位もできる人気の全身脱毛があり、さらに無料カウンセリング0円全身施術もたった60分で行います。
プライベートの予定もたてやすく、通っていただきやすいサロンとしても人気です。
また、脱毛しながら美容効果も期待できるイオン導入20倍のエレクトロポレーション脱毛も導入しており、脱毛だけでなく、美肌も手に入れることができます。
豊富なメニューを用意しているので、お肌にお悩みがある方や脱毛に興味がある方は、無料カウンセリングにお越しください。
プライベートの予定もたてやすく、通っていただきやすい
ストラッシュの川口店は、川口駅から徒歩3分の好立地に位置しているため、お客様が通いやすい環境が整っています。
また、脱毛施術が60分で全身61部位も受けられるため、お忙しい方でもプライベートの予定を立てやすく通っていただけます。
施術中には痛みが少ないため、お肌に優しい脱毛ができ、美容効果も期待できるので、お悩みがある方や脱毛に興味がある方にもおすすめです。
また、無料カウンセリングも行っているので、お気軽にご相談ください。
エレクトロポレーション脱毛も導入!脱毛しながら美容効果も期待
ストラッシュ 川口店は、全身脱毛サロンでありながら、美容効果も期待できるエレクトロポレーション脱毛も導入しています。
この施術は、脱毛しながらイオン導入20倍という美容効果も得られます。
つまり、脱毛と同時にお肌のお手入れもできるので、美しくつるつるの肌を手に入れることができるのです。
さらに、エレクトロポレーション脱毛は、産毛や日焼け肌にも効果が期待できるため、お肌に悩む方にもおすすめです。
全身脱毛、顔脱毛、VIO脱毛など豊富なメニュー
ストラッシュ川口店は、女性専用の脱毛サロンで、全身61部位を1度の来店で脱毛できる人気の全身脱毛ができます。
顔脱毛やVIO脱毛もメニューに含まれています。
また、産毛や日焼け肌でも効果が期待できるSHR脱毛を導入しており、肌が弱い場合や疾患がある場合でも施術が可能です。
さらに、同時に美肌も手に入れることができるイオン導入20倍のエレクトロポレーション脱毛も導入しているため、脱毛だけでなく美容効果も期待できます。
豊富なメニューが用意されているため、お肌にお悩みがある方や脱毛に興味のある方は、一度無料カウンセリングに足を運んでみてはいかがでしょうか。
一度無料カウンセリングにお越しください。スタッフがお悩みに寄り添います。
全身脱毛サロンのストラッシュ 川口店は、女性限定の脱毛サロンで痛みが少なく、産毛や日焼け肌にも効果が期待できるSHR脱毛を導入しています。
無料カウンセリングでは、お客様のお悩みや興味に合わせた丁寧な説明を行い、一緒に解決策を見つけていくことができます。
また、脱毛だけでなく、美容効果も期待できるイオン導入20倍のエレクトロポレーション脱毛も導入しており、同時に美肌を手に入れることができます。
豊富なメニューを用意しているので、お肌にお悩みがある方や脱毛に興味がある方は、ぜひ一度無料カウンセリングにお越しください。
スタッフがお客様のお悩みに寄り添い、キレイになるお手伝いをさせて頂きます。
未成年者もOK!保護者同伴もしくは同意書をご持参ください。
ストラッシュ川口店では未成年者のお客様も脱毛することが可能です。
ただし、保護者同伴での契約となります。
もし保護者様同伴が難しい場合は、同意書が必要です。
カウンセリング当日に保護者様の署名と印鑑付きの同意書をご持参いただけると、お客様自身で脱毛することができます。
同意書のダウンロードは公式ウェブサイトから可能ですので、ご利用ください。
日焼け肌でも大丈夫!安心して施術可能
ストラッシュ川口店では、日焼け肌の方でも安心して施術を受けることができます。
理由は、施術に使用するSHR脱毛が肌表面の色素に反応するものではなく、肌内部の毛包に働きかけるためです。
そのため、肌表面の色素に影響されることなく、安全に脱毛することが可能なんです。
また、低温での連続照射のため、従来の施術方法よりも肌トラブルが起きるリスクが低くなっています。
肌が弱い方や疾患がある方も施術をお断りする場合がございますが、ほとんどの方が安心して施術を受けることができるといえます。
ストラッシュ川口の口コミや評判を解説
夏のシーズンに向けて、女性たちは美しく輝く肌を手に入れるために、全身脱毛に挑戦している方も多いことでしょう。
そんな中で、注目されているのが全身脱毛専門店ストラッシュ川口です。
では、実際に利用した方々の口コミや評判はどうなのでしょうか?
今回はその点について解説していきます。
ストラッシュ川口で感じた驚きの美肌効果に密着!口コミレビュー
「ストラッシュ川口で感じた驚きの美肌効果に密着!口コミレビュー」とは、ストラッシュ川口という美容サロンで施術を受けた人が、その驚きの美肌効果を口コミで紹介したものです。
ストラッシュ川口は、肌のお悩みに応じて多彩な施術メニューを提供し、多くの人々から支持を受けています。
施術は、肌をキレイにするための最新テクノロジーや豊富な知識で、確かな美肌効果が期待できます。
その美肌効果について、実際にストラッシュ川口で施術を受けた人々が口コミでレビューを投稿しています。
投稿には、感動した美肌効果の写真や、施術中の様子なども掲載されており、非常に参考になる情報がたくさんあります。
ストラッシュ川口は、地域密着型の美容サロンとして、地元の人たちからの信頼も高いです。
また、専門のスタッフが丁寧にカウンセリングを実施し、お客様一人ひとりの肌のお悩みに合わせた施術を提供しています。
ストラッシュ川口で施術を受けて、その驚きの美肌効果を実感した人々の口コミレビューは、美容に興味のある人にとって、貴重な情報源となるでしょう。
是非、参考にしてみてください。
他店との違いはココ!ストラッシュ川口の全身脱毛に対する信頼度
ストラッシュ川口は、全身脱毛に特化したサロンです。
他店との違いは、プロフェッショナルな技術力、最新の脱毛機器、そしてお客様に対する信頼度にあります。
サロンでは、最新の脱毛機器を使用しており、痛みや肌荒れなどのリスクを最小限に抑えた脱毛を行っています。
また、脱毛に必要な回数や期間についても、丁寧にカウンセリングし、お客様に合わせたプランを提案しています。
さらに、ストラッシュ川口は、お客様に対する信頼度を大切にしています。
そのため、お客様がお肌のトラブルを感じた場合は、速やかに対応し、専門的なアドバイスを行っています。
さらに、万が一施術不足があった場合には、無料で追加施術を行う保証もあります。
このように、ストラッシュ川口では、お客様に最高の脱毛サービスを提供するために、技術力、脱毛機器、そしてお客様に対する信頼度にこだわっています。
他店とは違う、安心して全身脱毛を受けられるサロンとして、多くのお客様から支持を得ています。
料金も安心!ストラッシュ川口で全身脱毛&美肌ケアがお得に叶う!
「ストラッシュ川口」は、埼玉県川口市にあるエステサロンで、最新の脱毛マシンを使用して高品質な脱毛と美肌ケアを提供しています。
全身脱毛に加え、美肌ケアコースも充実しており、肌の悩みに特化したトリートメントも受けられます。
料金も安心で、初回限定で全身脱毛コースが10,000円(税抜)から受けられます。
また、全身脱毛コースと美肌ケアコースを同時に受けると、割引料金が適用されます。
施術には、脱毛エステ業界でトップクラスの脱毛マシン「SHR脱毛」を使用しています。
これは、痛みが少なく高い脱毛効果が期待できるマシンです。
また、スタッフも脱毛や美肌ケアに熟練しており、お客様のニーズに合わせたカスタマイズも可能です。
「ストラッシュ川口」で、安心で高品質な全身脱毛と美肌ケアを受けることができます。
処理時間が短くて効果的!ストラッシュ川口であなたもツルツル美肌に
「処理時間が短くて効果的!ストラッシュ川口であなたもツルツル美肌に」は、ストラッシュ川口で提供される脱毛エステサービスです。
このサービスは、処理時間が短くて効果的な点が特徴であり、貴重な時間を節約しながら美肌効果を実感することができます。
ストラッシュ川口では、最新の脱毛機器や技術を活用し、痛みを最小限に抑えながら確実にムダ毛を除去します。
そのため、多忙な現代人にとって、時間を有効的に活用しながら美肌を手に入れることができる理想的なエステサービスと言えます。
また、ストラッシュ川口は、多数のお客様から高い評価を得ており、自信を持っておすすめできるエステサロンです。
施術前には、丁寧なカウンセリングが行われ、お客様のニーズに合った最適なプランが提供されます。
さらに、ストラッシュ川口では、お得なキャンペーンや割引特典を定期的に実施しています。
これらの特典を上手に活用することで、よりリーズナブルに脱毛エステを受けることができます。
総合的に考えると、ストラッシュ川口の「処理時間が短くて効果的!
ストラッシュ川口であなたもツルツル美肌に」は、技術力に優れたエステサロンであり、お客様のニーズに合ったプランを提供することで、多くのお客様から高い評価を得ていることがわかります。
ぜひ、あなたもストラッシュ川口の脱毛エステサービスを利用して、理想の美肌を手に入れましょう。
施術前後のケアにも注目!ストラッシュ川口での全身脱毛が大人気の理由
ストラッシュ川口での全身脱毛が大人気の理由には、施術前後のケアにも注目が集まっています。
ここでは、なぜストラッシュ川口での全身脱毛が人気なのか、その理由を詳しくご紹介します。
まず、ストラッシュ川口では、施術前に必ずカウンセリングを行います。
カウンセリングでは、お肌の状態や脱毛による影響などをしっかりと確認し、お客様に最適な施術プランを提供します。
また、施術前にはお肌のケアも行い、脱毛前の確認やムダ毛の処理を行います。
そのため、お客様は安心して施術を受けることができます。
さらに、ストラッシュ川口では、施術後のケアにも力を入れています。
脱毛後には、お肌が敏感になっているため、クールダウンや保湿ケアを行うことで、お肌のトラブルを防止します。
また、お客様には、脱毛後の食事や生活習慣のアドバイスも行っています。
これにより、お客様が美しい肌を保つために必要な情報を提供することができます。
さらに、ストラッシュ川口では、美容全般についての知識を持ったスタッフが在籍しています。
そのため、施術中や施術前後に、お肌についての相談やアドバイスを行うことができます。
また、ムダ毛以外にも、美肌や美白、痩身など、お客様の美容に関する相談にも応じます。
以上のように、ストラッシュ川口での全身脱毛が大人気な理由は、施術前後のケアに注目が集まっていることが挙げられます。
お客様の美容に対するニーズに応えるため、スタッフが専門知識を持ち、施術前後のカウンセリングやアドバイスを行うなど、お客様にとっては安心して受けられるサービスを提供していることが、大きな魅力となっています。
ムダ毛とサヨナラ!ストラッシュ川口で充実の全身脱毛メニューを紹介
ムダ毛の処理は女性には欠かせない美容行為の一つですが、毎回時間と手間がかかるため、一度に全身を脱毛できるサロンに通うのがおすすめです。
川口にあるストラッシュは、全身脱毛メニューが充実しているため、効率的にムダ毛処理を行うことができます。
ストラッシュでは、痛みのない脱毛方法「エレクトロポレーション脱毛」を採用しています。
この脱毛方法は、肌表面で光を照射し、毛穴の奥のメラニン色素に働きかけて、毛を細くなりやすくすると同時に、肌にダメージを与えないのが特徴です。
また、女性らしい、繊細な部分の脱毛にも対応しており、VIO脱毛やウワサの全身脱毛も行っています。
全身脱毛は、1回ずつ処理する必要がなく、6回程度通うことで効果を実感できるため、忙しい女性にとっても通いやすいメニューとなっています。
ストラッシュでは、全身脱毛以外にも、ひげやわき毛、腕や足の脱毛など、部分的に脱毛を行うメニューもあります。
また、施術前にはカウンセリングを行い、施術の流れや痛みについてしっかりと説明してくれますので、安心して施術を受けることができます。
さらに、施術後にはアフターケアを行ってくれるため、肌トラブルの心配もありません。
ストラッシュ川口は、通いやすさや親しみやすいスタッフの雰囲気も好評で、口コミなどでも高い評価を得ているサロンです。
ムダ毛のお悩みを解決し、美しい肌を手に入れたい方は、ぜひ一度ストラッシュに足を運んでみてはいかがでしょうか。
ドキドキの初めてでも大丈夫!ストラッシュ川口全身脱毛初心者におすすめ!
女性たちが美しく輝くための脱毛メニューを提供しているストラッシュ川口店の初心者向けプランです。
初めて脱毛サロンを利用する方も安心して利用できる、ストラッシュ川口店の「全身脱毛初心者におすすめ!」プランには、顔・腕・脚・背中・お腹など全身を脱毛する施術が含まれています。
また、初めて脱毛をする方には脱毛の方法やアフターケアの方法などを詳しく説明した講習も行なっています。
ストラッシュ川口店は、脱毛の施術に最新の医療用レーザー機器を使用するため、非常に高い効果が期待できます。
また、脱毛によって皮膚にダメージを与えることもないため、肌への負担も最小限に抑えられます。
初めて脱毛をする方や、他の脱毛サロンで不満を持っている方にも、ストラッシュ川口店はおすすめです。
料金設定も分かりやすく、スタッフの方々も親切で丁寧な対応をしてくれます。
脱毛初心者にも優しいストラッシュ川口店で、ツルツルの美肌を手に入れましょう。
ストラッシュ川口店まとめ
ストラッシュ川口店についてまとめてみました。
ストラッシュ川口店は、全身脱毛サロンのストラッシュの店舗の一つです。
埼玉県川口市本町にあり、川口駅から徒歩3分の場所にあります。
営業時間は11:00?20:00で、年末年始以外は無休です。
全身61部位の脱毛ができるほか、顔やVIOなどの部位脱毛もあります。
料金は月額制と回数制から選べて、月額制なら全身脱毛が月々2,900円から受けられます。
最新のSHR脱毛器とエレクトロポレーション脱毛を使用しており、痛みが少なく日焼け肌にも施術可能で、美肌効果も期待できます。
カウンセラーやエステティシャンは女性のみで、衛生管理やスキンケアにもこだわっています。
以上がストラッシュ川口店のまとめです。
ご参考になれば幸いです。


